Explore our Free Cybersecurity and Risk Management Resources
Want to know more about vendor risk assessments and enterprise cybersecurity posture? Browse our range of security ebooks, guides, videos, and infographics, all created and verified by our expert team.
Browse resources

eBooks
Guides
Brochures
Whitepapers
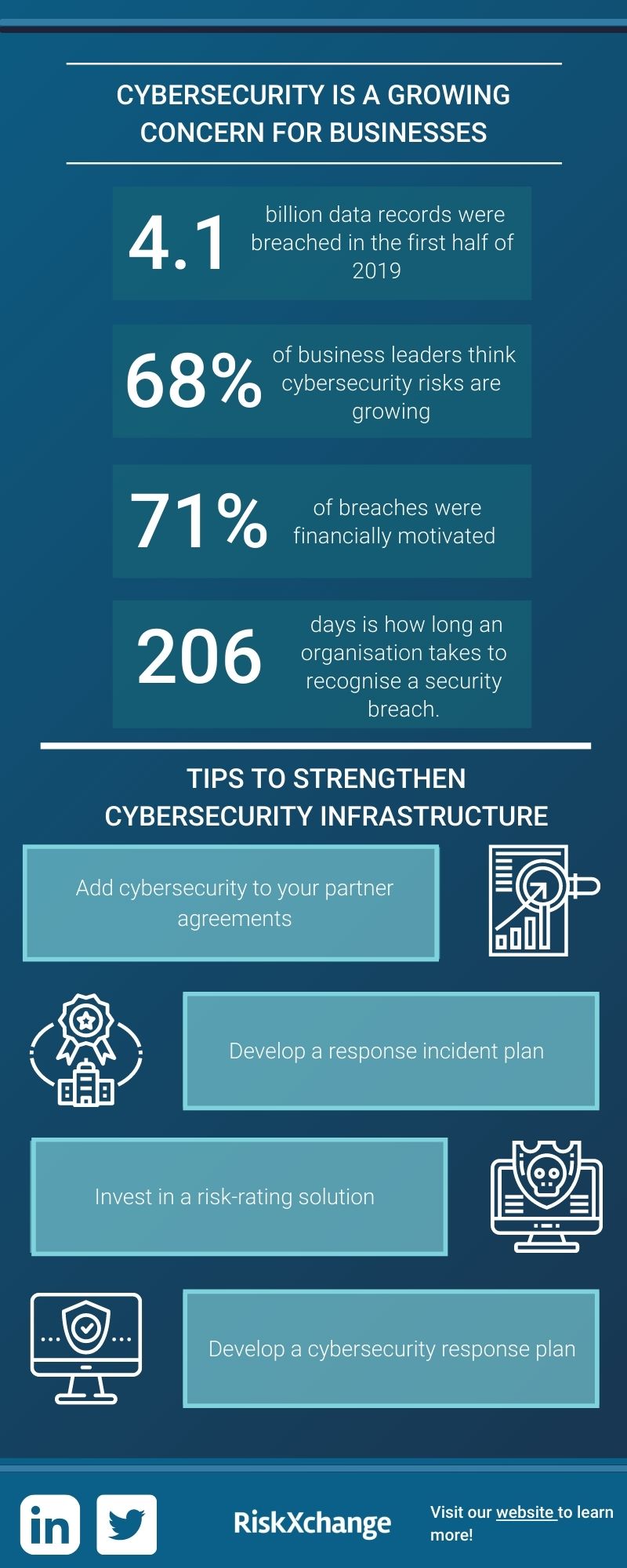
Infographics
Data sheets

RiskXchange and Ampliphae: Bring transparency, security, and compliance to your SaaS Platform
Download now
Webinars
360° Attack Surface Management: How to secure all your attack vectors
Implement DMARC the Right Way to Keep Phishing Attacks Out of Your Inbox
Advancing 3rd Party Risk Management and Compliance with RiskXchange
Understanding your Supplier & Technology Service provider Cyber Security Risks
Bridging the gap between third-party risk management and procurement
Insights for CISOs: Understanding how the right third-party risk management framework can boost data-driven cybersecurity decisions
Your third-party risk management framework can make or break your cybersecurity strategy
Navigating the cybersecurity challenges of an expanding digital ecosystem